Zero Trust Security: A New Cybersecurity Concept for Digital Businesses

Discover Zero Trust Security, a new cybersecurity approach that automatically trusts no one. Ideal for SMEs looking to protect critical data in the era of remote work. | Free Consultation KTN
Traditional Security Models Are No Longer Sufficient
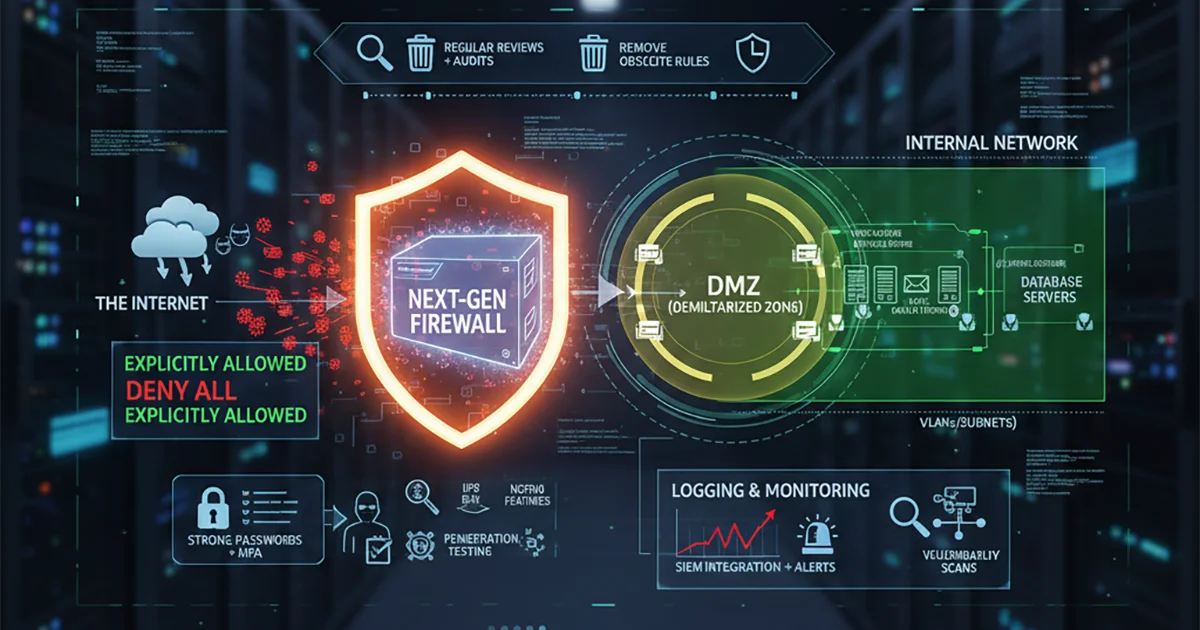
In an era where Remote work has become the norm, and cyberattacks are increasingly sophisticated, traditional security models relying solely on Firewall and VPN are no longer sufficient to protect critical organizational data. Many companies are now adopting the concept of Zero Trust Security, a security strategy that automatically trusts no one, not even internal users.
What is Zero Trust Security?
Zero Trust Security is a security concept based on the core principle: "Never Trust, Always Verify." This differs from traditional approaches where users, once authenticated into the corporate network, are automatically trusted. The Zero Trust concept assumes threats can originate from both outside and inside the organization. Therefore, every access request to data and systems must undergo strict authentication and verification, regardless of whether the user is inside or outside the network.
Key Principles of Zero Trust Security
1. Verify Explicitly (Verify Explicitly)
Every access request must undergo multiple forms of authentication, such as using Multi-Factor Authentication (MFA), device verification, and user behavior analysis, to ensure that the accessing party is legitimate.
2. Least Privilege Access (Least Privilege Access)
Users are granted access only to the data and systems necessary for their tasks, reducing the risk of misuse or attacks originating from compromised user accounts.
3. Assume Breach (Assume Breach)
Systems must be designed with the assumption that a breach could occur at any time. Therefore, network segmentation (Network Segmentation) and data encryption are essential to limit the scope of damage in case of an incident.
4. Continuous Monitoring (Continuous Monitoring)
Continuous monitoring and analysis of system activities help detect anomalous behavior and respond to threats promptly.
Benefits of Zero Trust Security for SMEs
- Reduce Cyberattack Risks: By verifying every access request, even from within the organization, it reduces the chances of hackers accessing critical data.
- Support Flexible Work: Ideal for working from home or other locations as it doesn't rely on traditional VPN.
- Protect Customer Data: Restricting access rights helps reduce the risk of personal data breaches, which could lead to PDPA issues.
- Control Unexpected Costs: Proactive prevention reduces costs associated with rectifying damage after an incident.
Steps to Implement Zero Trust Security
- Assess Assets and Risks: Understand which data and systems are most critical and identify potential vulnerabilities.
- Define Access Policies: Design rules specifying who should access which data.
- Deploy Security Tools: Select Zero Trust-compatible solutions such as Identity and Access Management (IAM), MFA, and threat detection systems.
- Train Employees: Raise security awareness within the team.
- Monitor and Improve: Regularly review performance and enhance the system.
Share this article
Admin User
Content Author
Related Articles